Have you heard of Office 365 Secure Score? We’ll explain what Secure Score is and how to use it to improve your organization’s security. Just to keep things real, we’ll use a real-world example. Volunteers, anyone? Anyone?
In this and subsequent articles we’ll explain what Secure Score is and how to improve your score, using CGNET as an example organization. Yes, this is a bit risky, since you’re about to see some of the areas we can improve upon (What? We’re not already perfect?)
What is Office 365 Secure Score?
We’re all familiar with credit scores–those numeric or red-to-green indicators of our creditworthiness, based on our credit activities and reports. Office 365 Secure Score is like a credit score for your organization. Secure Score observes what Office 365 services are in use, and examines the administrative settings for those services. Then it compares your settings to a Microsoft baseline for securing the services.
To access Secure Score, you have to have an Administrative role in your Office 365 tenant. To find Secure Score, select the Admin tile, then look for Security and Compliance as one of the administrative areas.
Secure Score in Action
Let’s start by examining CGNET’s Office 365 Secure Score; see the figure below.
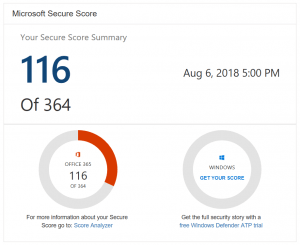
CGNET’s Secure Score
Hmm, looks like there’s some room for improvement here!
Fortunately, if we scroll down a bit, we see a list of action items that Microsoft has recommended, that would improve our Secure Score by T H I S much.
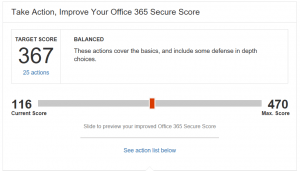
Suggested Actions from Office 365 Secure Score
Let’s take a look at one of these actions: client-side email forwarding rules.
Email Forwarding and Exfiltration
OK, even I had to look up exfiltration. Think of exfiltration as sneaking OUT OF the building. Kind of like when we would announce that we were leaving the R&D lab early on a Friday, because we had a “meeting” down the road at the manufacturing plant. Sure, there was an afternoon San Francisco Giants game that day, but that was totally a coincidence.
No, I’m not bitter. Not at all. Wish I would have thought of that…
We wouldn’t normally want to look into what our users are doing as the forward their emails. After all, we trust them as professionals. And now that we have OneDrive for Business up and running, we don’t have a need for users to forward documents as a way of collecting their work files for access out of the office.
As it turns out, however, the Bad Guys have figured out that this is an easy way to get access to an organization’s data. They’re breaking in by stealing someone’s credentials anyway. So it’s not much more work to set up an Outlook profile with the compromised user’s credentials, and then set up a client-side forwarding rule that sends everything of interest to an email address they control.
So this is now one of those behaviors that IT Managers have to monitor. You might start with just getting an alert whenever a client-side email forwarding rule has been applied. Or, if you’re more confident about who should be doing what with organizational data, you might go ahead and set up a rule that blocks this kind of forwarding in certain circumstances.
You’ll see here that Secure Score first explains the suggested remediation and how it would help improve your Secure Score.
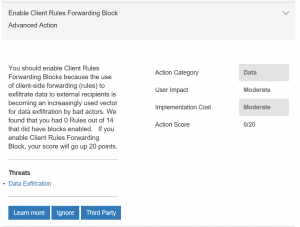
Explanation of Client Forwarding Rules Block
Then, if you click to “Learn More” you get a window that explains the action in more detail. At the end of the description, you can choose to Cancel out or Apply the remediation.
Azure Security Reports
I want to learn more about possible user impacts of blocking email forwarding. So I’m going to start with another action that has no user impact: reviewing Azure login reports.
Here’s the description.
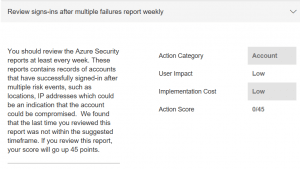
Review Azure sign-in’s action
And after I click “Learn More” I get this window.
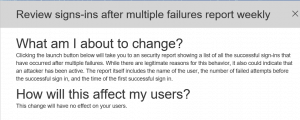
Azure Risky Sign In Report Explanation
From here, I click on “Review” and I’m taken to the Azure management console. As you’ll see, there haven’t been any risk sign ins so that’s encouraging.
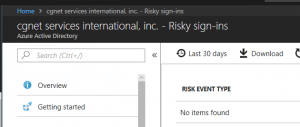
Azure Control Panel Review Risky SIgn-In’s
OK, so I’ll add this to our weekly log reviews. We’ll see how long it takes for the change to be reflected in our Secure Score.
We’ll look at some other security actions CGNET might take in our next article.





0 Comments