Last week we published an article on Secure Score (you can read it here). We wanted to use CGNET’s Secure Score and recommended improvements to show how Office 365 Admin’s can use it to improve security at their organization. We looked at email forwarding, but settled for now on reviewing Azure security reports. As you can see, our score improved by 66 points!

Now we’re going to look at multi-factor authentication (MFA) for our Office 365 Administrator accounts.
Setting MFA for Admin Accounts
Implementing MFA is a great idea for the entire organization: it’s a strong defense against breaches due to credential theft. But if that’s too big a step, at least get your Admin accounts set up with MFA. Why? Because Admin accounts hold the keys to many more information and network resources than the average user. If an Admin account is breached, things can go sideways in a hurry.
At CGNET we have an unusually large number of Office 365 administrators. We need to cover for one another, and (a bigger reason) we all want to learn about Office 365 by pulling on the administrative levers. I went to the Admin page and, under Users, selected the Global Admins view.
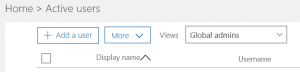
You can find Global Admins with a built-in view under Users
Still, it turns out that we had four Admin accounts that did not have MFA enabled. One account was no longer in use and I was able to delete it. The other three accounts look like generic accounts (they’re not tied to specific users). So I am going to have to check with our technical folks to see if these accounts are still needed. If they are, then we’ll want to enable them for MFA as well.
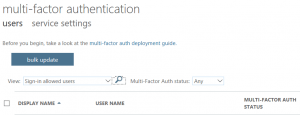
See a list of users and their MFA status
This earns us an additional 11 points (yes, I’m competitive and can be “gamified”) but it’s worth doing regardless of the Secure Score improvement. There are too many stories of networks that got hacked because someone found one of these generic accounts and either had the password or was able to easily guess what it was.
A Call to Action
Give this a shot. If you want to organize your approach to MFA, here’s a nice article. First, find out what accounts are assigned Global Admin (or any Admin) status and critically review the list. Hint: look for contractor accounts that don’t need to have administrative privileges anymore. Next, enable multi-factor authentication for those accounts. You’ll sleep better tonight.





0 Comments